Research on Information Hiding Technology Based on Color Static Digital Image(1)
The digital image information hiding technology is one of the most challenging and most active research topics in the field of digital image processing. This paper outlines the information hiding technology of digital images and presents a new information hiding algorithm based on color still digital images.
1 Introduction
With the rapid development of the information industry represented by microelectronics technology, multimedia, computer networks, and personal mobile communication technologies have entered the homes of ordinary people, and digitalization has been deeply rooted in people's minds. The Internet-led wave of networking has swept the world. According to statistics, among the various kinds of information collected through sensory organs in people's daily lives, the most important one is visual information. Then, in digital life, digital images become the most important form of information that people perceive [1].
Digital images can be classified into two types: still images and dynamic images. The latter are generally called video images. Each frame of a video image can be regarded as a still image, but these still images are not isolated from each other but exist on the time axis. A still image is a set of pixels. The actual distance between adjacent pixels is called the spatial resolution of the image. According to different pixel color information, digital images can be divided into binary images, grayscale images, and color images. The final sensation of the digital image is the human eye. The pixel values ​​of two very similar digital images perceived by the human eye may vary greatly. In this way, relying on the imperfection of Human Visual System (HVS) provides a tremendous space for distortion and information hiding of digital images.
Information hiding and information encryption are different, information encryption is the content of hidden information, and information hiding is the existence of hidden information. Information hiding is more secure than information encryption because it does not easily attract the attention of attackers.
2 Information Hiding Technology Overview
2.1 Information Hiding Introduction Information Hiding, also known as Data Hiding, or Digital Watermarking. In simple terms, information hiding refers to embedding a signal (generally referred to as a signature signal) into another signal (generally called a main signal, Host Signal, or a cover medium, cover- In the media process, the cover media becomes a stegano-media after embedding the information. This embedding process needs to meet the following conditions [3]:
The imperceptibility of the signature signal. In other words, after the signature signal is embedded, the perceived characteristics of the main signal do not change significantly, and the signature signal is “hidden†by the main signal.
The robustness of the signature signal (Robustness). The various distortion transformations of the signature signal to the main signal, such as distortion signal compression, affine transformation, noise addition, A/D or D/A conversion, and various malicious attacks, should all reflect certain Robustness. Unless the perceived nature of the primary signal is significantly compromised, the signature signal will be difficult to remove.
In general, the embedding of the signature signal does not increase the storage space and transmission bandwidth of the main signal. In other words, after the signature signal is embedded, it is hard to perceive the change of information on the “surfaceâ€.
The history of the development of information hiding can be traced back to the use of "Steganography". The term "concealed" is derived from the combination of the words "hidden" and "graphic" in ancient Greek. Although both "hidden technique" and "cryptography" are confidential technologies that are dedicated to information, their design concepts are completely different. "Cryptology" is mainly designed to make encryption information unreadable, but for non-authorized persons, although he cannot know the specific contents of confidential information, he can be aware of the existence of confidential information. The "shadow technique" is devoted to designing exquisite methods so that non-authorized persons have no way of knowing whether or not confidential information exists. Compared with modern cryptography, the greatest advantage of information hiding is that it does not limit the access and access to the main signal, but is dedicated to the security of the signature signal.
2.2 The basic framework of the information hiding algorithm The following section gives the basic framework of the information hiding algorithm based on the orthogonal transformation, including the embedded process and the detection process, as shown in Figure 2.1 and Figure 2.2.
Algorithm 2.1 (Change-domain based information hiding embedding algorithm)
Performs orthogonal transformation of the original main signal;
Perform a perceptual analysis of the original master signal;
On the basis of step (2), the signature signal is embedded in the main signal in the transform domain based on the key given in advance, and the main signal with hidden information is obtained.
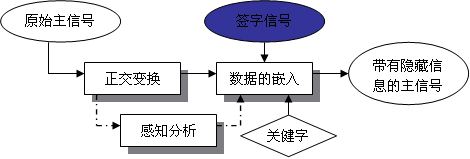
Figure 2.1 The process of embedding an information hiding algorithm
We focus on doing Custom Drawstring Bags service. Our drawstring backpack already export to many countries. We have a team of senior engineers and skilled craftsmen, who can comply with customer's design and specification to produce, also can design and produce for our customers. Whether Cinch Bags for a long trip or gathering your equipment for the gym, drawstring bags may be all you need to get your belongings from point A to point B. They come in all sizes from tiny to over 75 cm tall.Choose from a plain cotton drawstring bag or look for name brand products. Some even have the option of personification. Store your stuff in this easy compact manner.
Drawstring Bags General Order Information
We take great pride in our work and in the wide variety of Drawstring Bags that we offer. We are experienced in servicing the US market, European market and Africa market .Please be aware that our production lead times depend on specific drawstring backpack and drawstring backpack quantities. Our success has been based on our understanding of the demands and nature of promotional and marketing deadlines. That's why we always ensure that every order is delivered on time.
As a result of our high quality products and outstanding customer service, we have gained a global sales network reaching. The main exporting products are promotional bag, jewelry bag, shoe bag, travel bag, school bag, Shopping Bag, drawstring bag, cooler bag, backpacks, cosmetic bag, wallet and so on.
If you are interested in any of our Drawstring Bags or would like to discuss a custom order, please feel free to contact us. We are looking forward to forming successful business relationships with new clients around the world in the near future.

Drawstring Bags
Sports Drawstring Bags,Drawstring Handbags,Custom Drawstring Backpack,Printed Drawstring Bags
WenZhou JinYuan Packing Manufacture Co.,Ltd , http://www.tote-shoppingbag.com